More Than NACLs

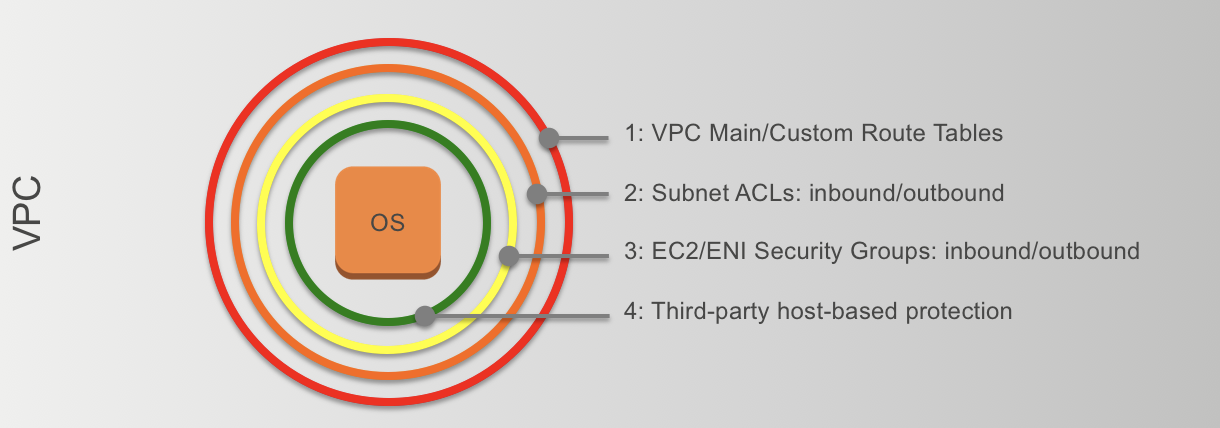
The virtual network in the cloud can be secured at different levels, as shown within the picture.
| Security Group | Network ACL |
| Operates at the instance level (first layer of defense) | Operates at the subnet level (second layer of defense) |
| Supports allow rules only | Supports allow rules and deny rules |
| Is stateful: Return traffic is automatically allowed, regardless of any rules. | Is stateless: Return traffic must be explicitly allowed by rules |
| We evaluate all rules before deciding whether to allow traffic | We process rules in number order when deciding whether to allow traffic |
| Applies to an instance only if someone specifies the security group when launching the instance, or associates the security group with the instance later on | Automatically applies to all instances in the subnets it's associated with (backup layer of defense, so you don't have to rely on someone specifying the security group) |
Routing table rules can be used to take advantage of the positive aspects of the two tools described above. Ok, it is not a great discovery but nevertheless the features I will talk about later are not often used.
| Routing Table |
|---|
| Operates at the subnet or VPC level (second or third layer of defense) |
| Supports allow rules and deny rules |
| A rule enables bidirectional traffic, or only outbound |
| We evaluate all rules before deciding whether to allow traffic |
| Automatically applies to all instances in the subnets it's associated with |
DENY RULE: Suppose you want to enable all inbound/outbound traffic from a subnet except for a certain IP address.
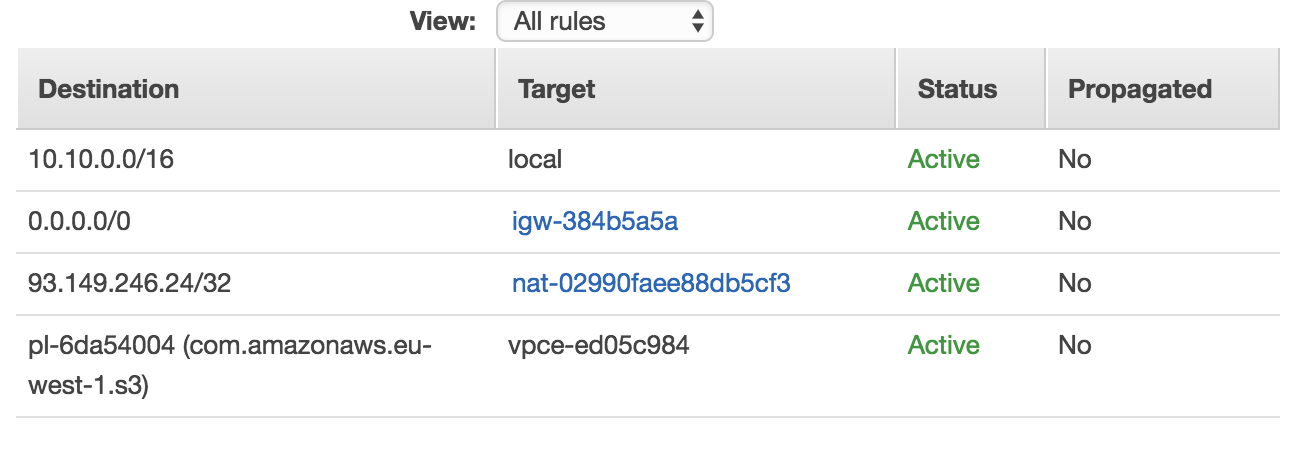
This overrides the NAT rule because it is more stringent, so the address 93.149.246.24/32 will not be able to reach any EC2 on the subnet unless the machine in question initiates communication to the first address.
ALLOW RULE: Suppose we want to allow only one IP address access to the subnet and deny traffic to all others.
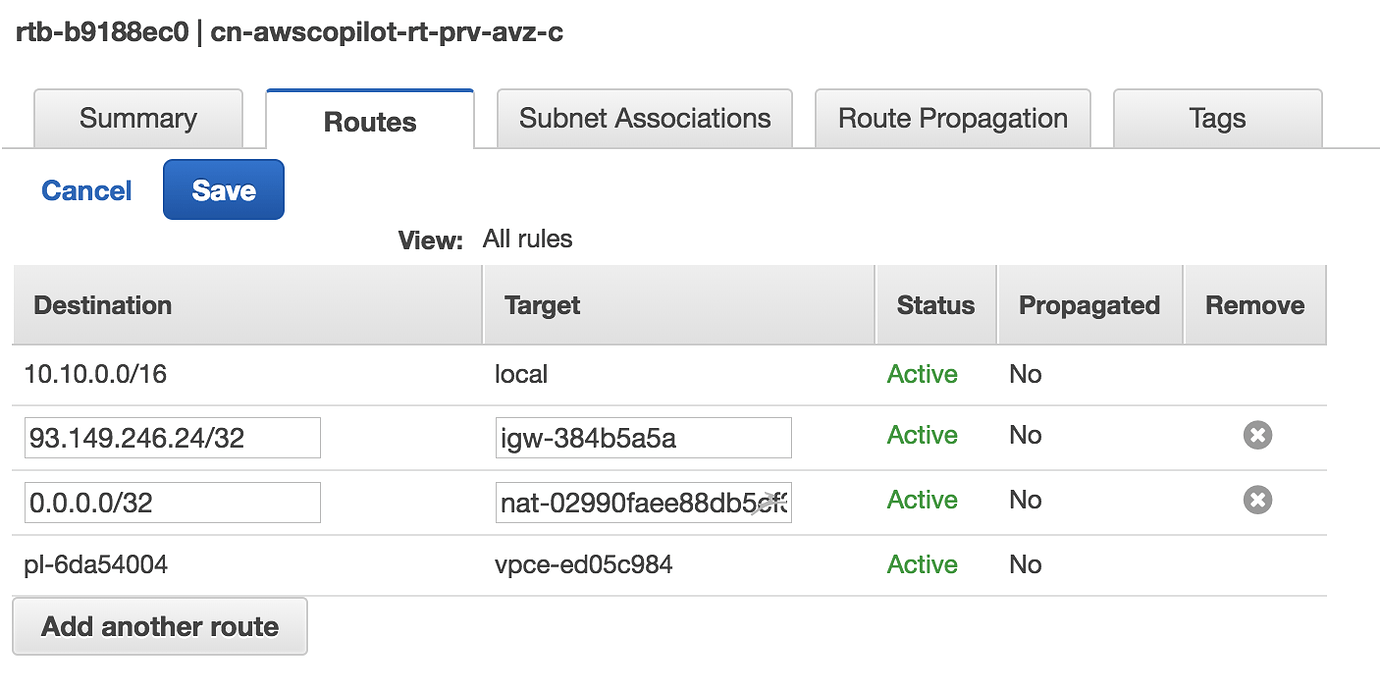
In this way, the address 93.149.246.24/32 is the only one that can access the machines in the private network without necessarily going through the bastionhost.
Conclusions
In conclusion, NACLs offers a robust set of features, including subnet-level protection, high performance, and support for both allow and deny rules. Additionally, it provides a stateful layer of defense similar to Security Groups and prioritizes the most strict rule, also like Security Groups.
- Subnet-level protection, like NACLs
- High Performance, like NACLs
- Supports allow and deny, like NACLs
- Stateful layer of defense, like Security Group
- The most strict rule wins, like Security Group
However, it's important to note that the configuration discussed in this post is only suitable for testing purposes. When configuring Network Firewall for production environments, careful consideration should be given to the specific needs of the network and application to ensure proper security measures are in place.